Description
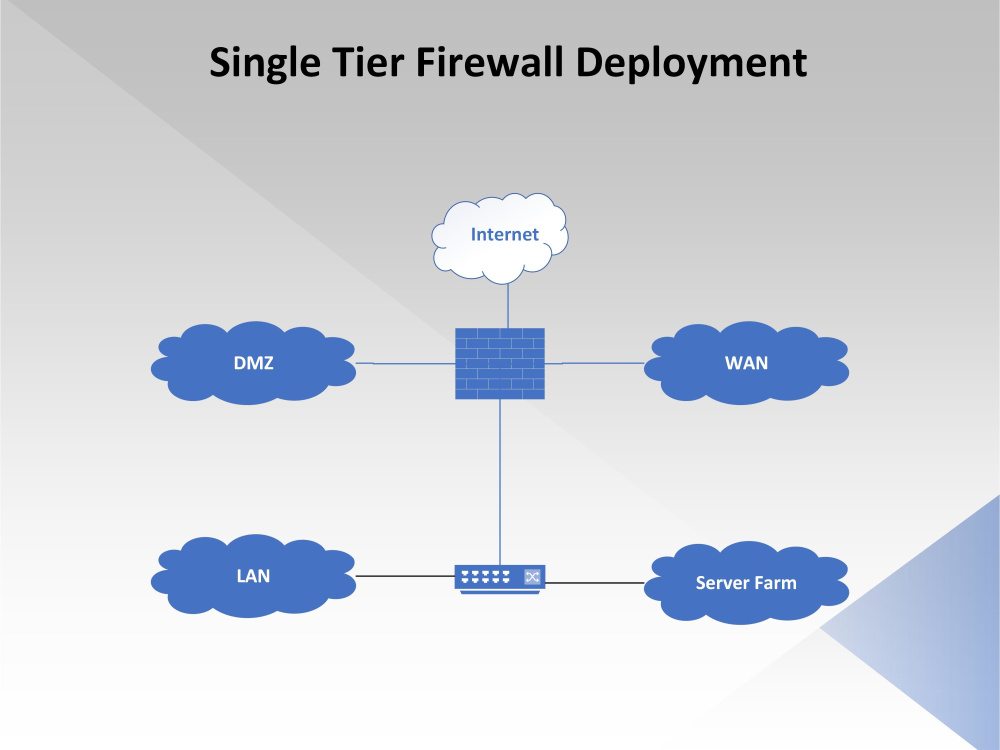
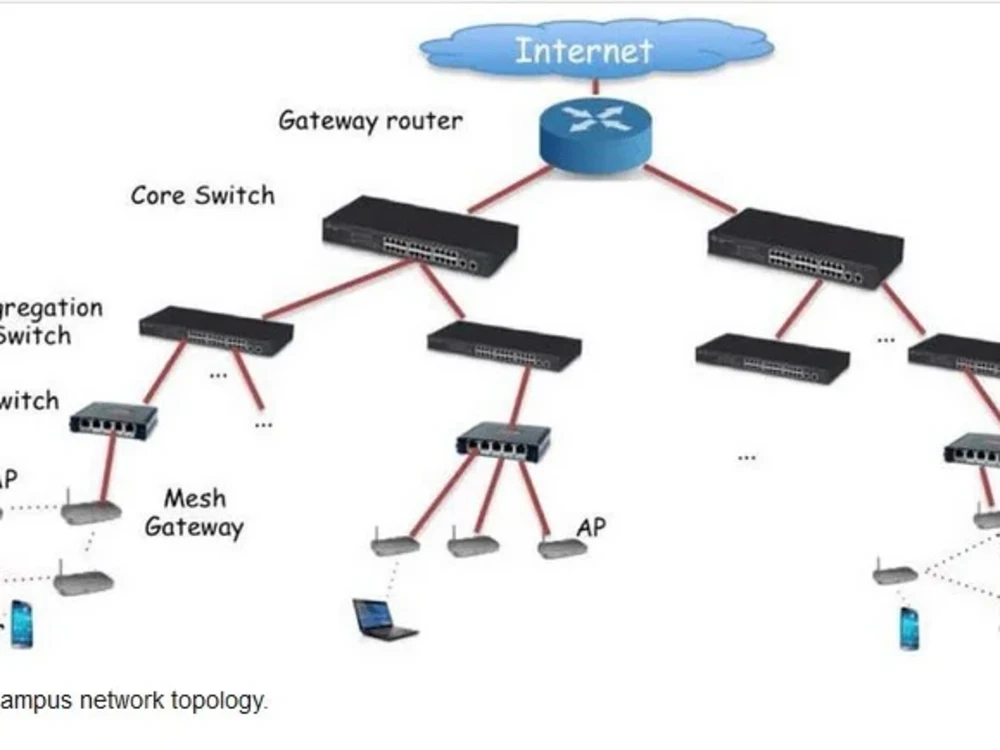
Our Firewall Configuration service provides a robust line of defense for your network by setting up, optimizing, and maintaining firewalls according to industry standards. We begin by evaluating your network architecture and current security measures. Then we design a firewall policy aligned with your specific operational requirements. This includes configuring access control lists, NAT rules, intrusion detection/prevention systems, and logging mechanisms. Our team ensures minimal downtime and seamless integration with your infrastructure. We also provide monitoring and periodic audits to ensure your firewall evolves with your business.



Mayowa –
Firewall Configuration offers a solid, centralized platform for managing complex security rules. Its intuitive interface simplifies policy creation and enforcement across diverse network environments. While reporting could be more granular, the solution delivers effective protection and streamlines firewall administration tasks, contributing to improved overall network security posture.
Fatima –
Firewall Configuration streamlines complex network security management. The intuitive interface simplifies policy creation and enforcement, while comprehensive reporting offers valuable insights into network traffic. It’s a solid solution for organizations seeking to improve their firewall rule management and overall security posture.
Umma –
Firewall Configuration provides a centralized platform for managing complex firewall rules across multiple environments. Its intuitive interface simplifies policy creation and auditing, enhancing network security and compliance. The solution offers robust logging and reporting features, enabling quick identification and resolution of potential threats. It’s a practical tool for organizations seeking streamlined firewall management.